9 Best Penetration Testing Tools – For the best online penetration testing service provider, the right kind of tools makes all the difference between the success and failure of a testing procedure. The goal of a penetration testing exercise is to simulate as realistic a hacking attempt as possible so as to uncover all potential vulnerabilities.
Gone are the days where hacking was a complicated exercise – in today’s world, there are a full suite of tools and tried-and-tested techniques for hacking into any software or application. Therefore, regular penetration testing will ensure that the testing team stays ahead of such malicious activity and keeps business interests and operations protected.
9 Top Penetration Testing Tools Used
As we talked about before, there are a set of penetration testing tools that make every tester’s job easy while ensuring that all potential vulnerabilities are exploited properly. Some of them are as below:
1. nmap
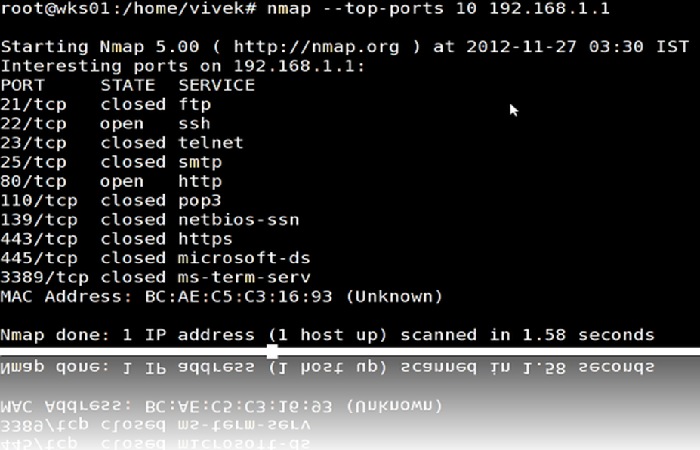
One of the most popular options for a port scanner in network penetration testing, nmpa (or network mapper) maps out all the available ports, the ones that are open, and what they are used for. It’s best used during the reconnaissance phase to collect information on potential vulnerabilities which provides an accurate picture on public security.
2. Wireshark
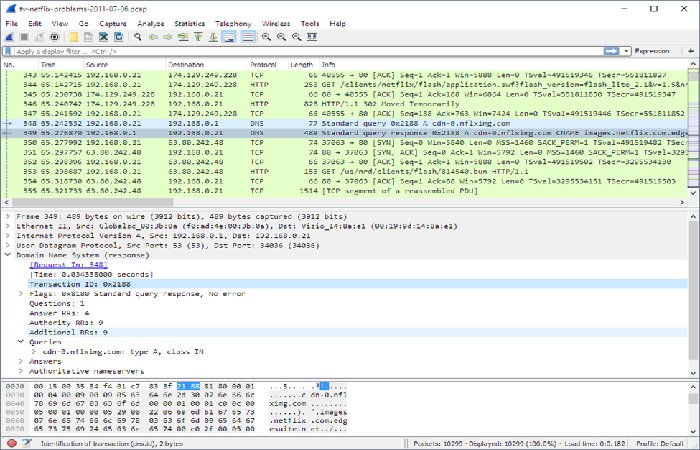
Wireshark is a network protocol analyzer used to gain insights into the kind and amount of website traffic passing through the network. It’s best used for analyzing TCP/IP connectivity issues, combining this with the real-time analysis of different kinds of protocols. It also provides decryption support for these protocols and is thus used widely by both amateur and experienced pentesters.
3. Kali Linux
If you’re looking for foundational support throughout the penetration testing procedure, look no further than this tool. Many pentesting teams use Kali Linux as their base pentesting system unless the testing scenario is more customized and requires specialized knowledge or you’ve enough knowledge to design each testing process. The tool functions best as an offensive strategy and can be run on the company’s hardware.
Some pentesters even use the Kali virtual machine on the Windows or OS X operating systems. Kali Linux bodes well with most pentesting tools and is the default option for pentesting procedures but since it’s an offense-based tool, it can get exploited in return. Therefore, no sensitive files or business secrets should be stored on the Kali virtual machine.
4. Hashcat
With expertise on password recovery utility, Hashcat is one of the more popularly used pentesting tools for cracking hashes, password-cracking brute force attacks, dictionary and mask attacks, etc. Pentesting usually involves breaking into hashed passwords and using these credentials to break into the system for which this tool is ideal. Hashcat is supported on the CPU and GPU, but it works significantly slower on the former.
5. Burp Suite
Burp Suite functions as a web vulnerability scanner and is mostly used by the pros since many of its best features are included in the paid version. The tool has created a niche for itself in the web security and penetration testing community with multiple options for testing different applications and assets.
6. sqlmap
SQL injection attacks are considered to be highly dangerous since hackers gain entry into the database with the possibility of manipulating internal systems and assets. sqlmap is designed to effectively target the potential for such kinds of attacks through an automated process that detects and exploits flaws leading to the takeover of the database servers. It’s trained to target the usual targets such as Firebird, Sybase, Oracle, PostgreSQL, Microsoft SQL Server, etc.
7. John the Ripper
This tool is aimed at effectively cracking encryption within the maximum capacity of your GPU and is also an open-source tool, which allows for offline password cracking attempts. Adopting the style of brute force and DoS attacks, it uses a combination of letters and symbols in order to crack the credentials and rearranges them till the attempt is successful.
8. Metasploit
After defining your intended target, picking the ideal exploitation method, choosing the right payload, Metasploit allows you to design the perfect penetration testing procedure. Its greatest strength is the automation of repetitive and simplistic tasks which shows us why it’s the preferred penetration testing framework among most service providers.
9. Hydra
A great accompaniment to John the Ripper, Hydra is also used as a password cracking tool, specialized to crack through the SSH/FTP login, IMAP, RDP, etc. It can use a particular combination of letters and/or symbols and use it to crack the intended target. The tool provides proof as to why it’s important to place limits on login attempts and necessarily disconnect users after a defined number of times for better protection against hackers.
These are only some of the many penetration testing tools widely used by third-party service providers. It’s equally important to choose the right kind of cybersecurity expert for conducting the procedure to ensure optimal rates of success.